For 5.04 billion people worldwide, social media is a part of daily life, used to connect with others and find information. The openness and trust that make social media a space for making connections also expose it to risks, with it becoming an excellent place for threat actors to conduct surveillance.
Information we share, such as the first car we drove or the people we follow, can give threat actors the information needed to breach accounts and conduct phishing attacks. As a business leader, it is important to know that social media is not a domain restricted to your team’s personal lives; the information that threat actors gather on these platforms can also put your business at risk.
Phishing attempts on social media
Social engineering and impersonation were the second most common forms of malicious or criminal attacks reported to the Office of the Australian Information Commissioner (OAIC) between July and December 2023. Threat actors use social media to conduct phishing attacks, often sending automated messages with fake offers or customer service inquiries to large numbers of users. However, attackers sometimes target specific individuals more directly, using fake or stolen profiles to gather business-related information.
Minimising the impact of phishing attacks starts with educating users to be wary of any suspicious communications they receive, whether via a business email during work hours or on their personal social media accounts after hours.
Types of malicious or criminal attacks reported – July to December 2023
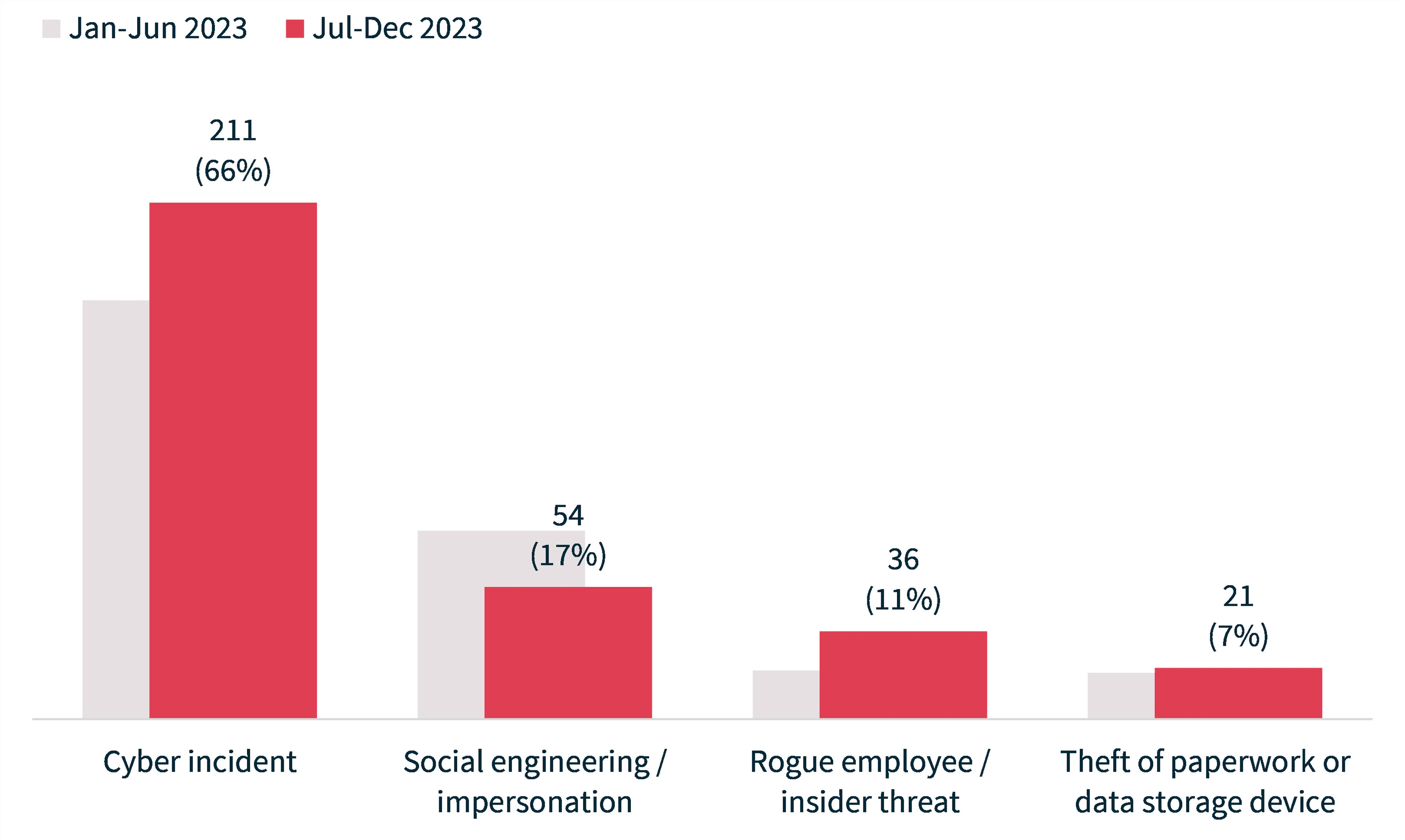
Source: OAIC.
Using social media profiles to gather data
Threat actors use social media to perform detailed reconnaissance on businesses and employees. They can exploit social media to:
Gain answers to security questions: Social media quizzes and posts that prompt users to share personal details like travel history, favourite colours, or pet names can inadvertently supply hackers with the answers to passwords or security questions.
Research specific team members: Threat actors can use social media to find people in senior positions or with access to sensitive data and target them in spear-phishing attacks. This strategy increases the credibility and success rate of these attacks.

Impersonating social media profiles
Threat actors also use social media as an impersonation tool, taking over existing accounts or creating clones resembling legitimate accounts. This tactic is one way to increase the success of phishing attempts. When taking over accounts, attackers control a social media page and reach out to colleagues, followers, or partner organisations to phish for sensitive information. They send out fraudulent messages from these compromised accounts that look legitimate, increasing the chances that recipients will trust and respond to them.

Conclusion
Emails and texts are not the only modes of communication that threat actors use to phish people; your team must understand that suspicious messages on personal accounts could be attempts to exploit the business. Information shared online can also help cyber criminals identify potential targets or gather details about your business. This information will inform phishing attempts and allow threat actors to make them believable.
Layer 8 can boost your team’s awareness of social media risks
Our Cyber Escape Rooms provide an immersive experience that blends kinesthetic, auditory, and visual stimuli to embed cyber security knowledge throughout your business. These sessions also serve as enjoyable team-building exercises that use gamification techniques to boost knowledge retention and strengthen cyber security practices. Visit our Cyber Escape Room page for more information and to book a preview session.
Related blogs
Maximising device security: 3 habits your team should implement
5 ways to revitalise your team’s cyber security habits in the new year
Where your current cyber security training program falls short





