Has your organisation accounted for the cyber security concerns created when hybrid working?
Securing your hybrid workforce starts with securing the human factor. Hybrid workforces can introduce vulnerabilities such as unsecured networks and social engineering. In FY 2023, the Australian Signal’s Directorate (ASD) found that the top three cybercrime types affecting businesses were email compromise, business email compromise (BEC) fraud, and online banking fraud. Attacks like these become much easier to execute when teams work separately and become used to verifying requests digitally. Minimising risks like these starts with strong security practices that your team can adopt at home or in the office.
Cybercrime types in FY 2023
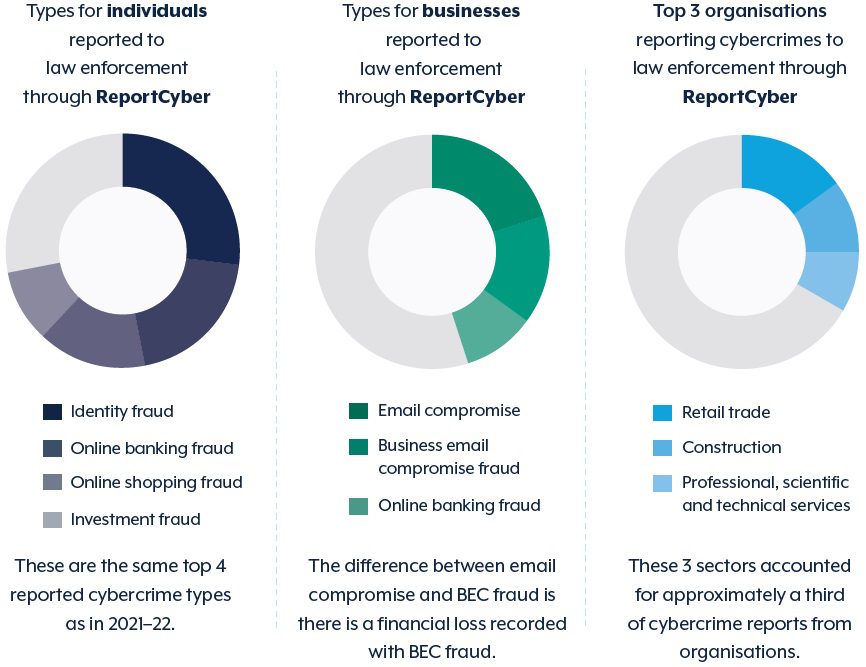
Source: ASD.
Threats that arise when hybrid working
Hybrid working presents unique challenges to cyber security. This model increases the risk of cyber threats for several reasons:
- People use various devices connected to multiple networks, from personal smartphones to company-provided laptops. Each device and network potentially offers a point of entry for threat actors, making it harder to secure data consistently.
- Social engineering attacks can be more successful in hybrid work. In a traditional office setting, verifying the authenticity of a request could be as simple as tapping a colleague on the shoulder and having a chat. In a hybrid model, the physical separation and increased digital communication make it easier for attackers to impersonate colleagues in emails or messages.
- Home networks often lack the security measures typically enforced in office environments, such as advanced firewalls and intrusion detection systems. When employees connect to corporate resources from unsecured networks, they inadvertently create gateways for attackers to access organisational data.

Strategies for securing hybrid work
Conducting phishing simulations
Regular phishing simulations are essential for educating employees about the nuances of identifying suspicious communications. These tests raise awareness and help pinpoint employees who may require additional training. Identifying these individuals isn’t about shaming them but highlighting opportunities for further learning to strengthen the company’s overall cyber security posture.
Outlining an incident response plan
Only 36% of executives in a PwC survey noted that their company had a disaster recovery and backup plan that they revisit and update. A clear and actionable incident response plan enables your organisation to manage and mitigate cyber threats. This plan should include clear procedures for team members to report suspicious behaviour. A quick response reduces potential damage from a security breach, limiting data loss and financial impact.
Protecting home networks
Your team should be aware of best practices for securing home networks. Team members should ensure their network is password protected, with only trusted people accessing the login details. IoT devices connected to the network can also become a vulnerability if a threat actor compromises them with malware. Team members should review the device’s security settings to determine whether it really requires an internet connection to use.

Conclusion
Hybrid work expands the attack surface and provides opportunities for threat actors to socially engineer your team or exploit networks. Measures like conducting phishing simulations, developing an incident response plan, and securing home networks can mitigate threats. Training and reminding your team of best practices can strengthen your organisation and mitigate risks.
Why choose cyber security training with Layer 8?
Our innovative, gamified training approach blends the excitement of escape rooms with comprehensive cyber security education, creating an engaging learning environment. Visit our Cyber Escape Rooms page for more on our interactive approach and to schedule a preview session.
Related blogs
Maximising device security: 3 habits your team should implement
Where your current cyber security training program falls short






