Cyber security threats have increased alongside the growth of hybrid and remote workforces, challenging organisations to stay ahead and reinforce defences. In FY2023, Australian businesses reported over 1,100 cyber security incidents to the Australian Signals Directorate (ASD), and law enforcement received nearly 94,000 reports. Despite technology being a gatekeeper for cybercrime, it alone isn’t always enough; teams must also be vigilant. This blog covers how team training can transform your employees into a human firewall and protect remote work operations.
Understanding the human firewall
A human firewall refers to your employees’ collective cyber security awareness. Where software firewalls block threats at the network level, human firewalls deal with threats through learned actions and decision-making. Training your team to recognise and respond to cyber threats is crucial in an era when remote work blurs the boundaries of secure office environments and potentially vulnerable home networks.
How regular training builds the human firewall
A well-built human firewall starts with regular training programs. Whether working at home or in the office, cyber threats constantly evolve, with malware variants and new phishing scams emerging regularly. Holding frequent training sessions ensures that your staff can identify and mitigate risks. Training should include practical simulations and up-to-date information on the latest threats.
Creating a cyber security culture
Team training contributes to building a cyber security culture. To be successful, this culture requires a top-down commitment to cyber security across all staff and teams. Leadership should participate in team training and model secure behaviours. Doing so will foster an environment where cyber security becomes integral to everyday operations. Encouraging open dialogue about security practices and recognising employees who exhibit exemplary vigilance can strengthen this culture.
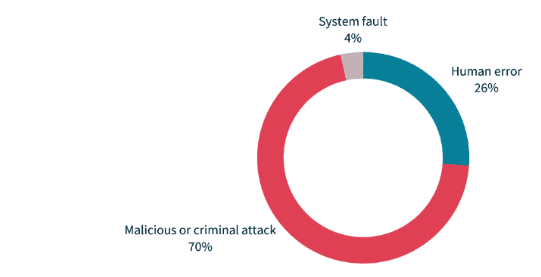
Sources of data breaches – July to December 2023.
Source: OAIC.
Implementing effective security practices for remote work
Working remotely can introduce unique challenges like unsecured networks and personal devices. To counter these, train team members on adopting key security practices, including:
- Secure access: Encrypt data transmissions between employees’ devices and your company network through a Virtual Private Network (VPN).
- Device security: Require staff to use antivirus software on all work devices and encourage strong password policies.
- Secure networks: Request that staff secure their home network with a password and do not leave the access details in easy-to-find locations.
Measuring and improving team training
Team training does not stop after one session. Track key metrics such as the number of security incidents, employee compliance rates, and phishing simulation results. Regularly reviewing these metrics allows you to refine your training approach, keeping it relevant and impactful.
Conclusion
In any hybrid or remote working landscape, your employees are your first line of defence against cyber threats. By fostering a culture of security and hosting regular, engaging training, you can transform your team into a human firewall. This proactive approach protects your organisation and keeps your workplace and business ahead of cyber attacks.
Why choose Layer 8 to help build your human firewall?
Boost cyber awareness within your organisation through immersive and team-building training activities that empower staff to confidently prevent attacks before they take hold of your business. For more information, visit our guides on world-class cyber awareness training or enjoy our unique Cyber Escape Room experience for staff training.
Related blogs
Safe at Home and Work: Understanding Cyber Security in a Hybrid World
Maximising device security: 3 habits your team should implement
Where your current cyber security training program falls short